#SQL import
Explore tagged Tumblr posts
Text
Quick guide on creating MySQL databases, setting up users with passwords, reloading MySQL services, and import SQLdump file.
#database creation#database management#MySQL#SQL#SQL import#SQLdump file#SQLdump import#user permissions#web hosting#website administration
0 notes
Text
Slammer Sonic/Slammer Worms Lore
Slammer Worms can completely devour/corrupt a game however can trick a player/pc owner into seeing the game as normal.
However, a keen eyed player will notice all the character's sprites being more monochromatic in color if Slammer has been there, they also seem to lose idol animations, and only move if scripted or if the player makes them.

What happens if Slammer fully consumes a game? Well you know how you can't eat the same exact pizza over and over again?
If a game is destroyed on a computer, you can't simply delete and reinstall it on that computer, no matter where the source is from, that game on THAT computer is ruined forever.
But if Slammer Prime/a Clone finds a whole new computer, they can eat the same game again, since it's a fresh PC to work with.
So in a technical sense, many Slammers can come from Sonic CD, but often prefer to explore other games in the same series just for a tad of Verity.

Slammer Prime and the clones all have some things in common, to tell themselves apart from eachother, but also other computer virus and horror au chararters.
Slammer Prime and the clones all have golden shoes, all of them have the same type of Blue Slammer Prime ((aka Slammer Sonic)) somewhere on them.
The Slammer Clones and Slammer Prime also all share an insect theme, before entering a game.
A Clone can choose what type of insect they wanna be, and as long as that insect is worm like during one stage of it's life. Then they can become it upon entering the game world.
Here are some examples.
Slammer Prime is (earth worm) based.
Slammer Tails is (wasp) based, wasps count because they are larva at some point.
Slammer Shadow is (Moth) Based cause Moths have caterpillar forms before they become moths.
The final thing that helps keep each Slammer different then another Slammer is the fact, every single clone has a different video game character host.
No Two Slammers can share the same character as a host, even if from a different game.

However there is ONE other example of a Slammer Sonic, and that Clone belongs to the playground au owned by misscloudiedays.
Playground Slammer is NOT connected to the other Slammers.

Slammer Prime and the Slammer Clones work alot like a hive mind.
They can act independently however they are all connected to eachother, as soon as a Slammer clone get's a host, and finish consuming the game they are in, they are connected completely to the other Slammers and are given access to the same powers and abilities as all other Slammers.
All Slammer clones are at the same power level, once they have connected properly but all are weaker then Slammer Prime.
Upon a Slammer Clone or Slammer Prime consuming a new virus/more code the new information is shared among all of them.
If a Slammer Clone is Killed somehow, the other clones will track it's remains to devour it, and that clones host can be given to another Slammer Clone.

Playground Slammer Sonic, Slammer Amy Rose, Slammer Shadow The Hedgehog.
Are the only Slammer Clones disconnected from the hive, each with their own reasons.
Playground:
unwillingly separated due to the fact all horror entities are made into harmless toddler versions of themselves, because of how this au functions.
Slammer Amy: Willingly separated this is one rare case where the clone spawned into existence with an 'empathy virus'
There is a 0'01% chance for a Slammer Clone to spawn itself with a virus that can either hinder it or make itself stronger.
This Slammer Clone had one that gave it empathy, so it willingly disconnected itself from the hive and share's control with Amy herself.
The only thing it forces amy todo is eat flicky's.
Slammer Shadow: Unwillingly
(unknown why disconnected from hive)

Slammer Prime and Slammer Clones all go by it/its/they/them before they get a host.
Once they have a host, they steal the hosts pronouns as their own.
Best Examples being
Slammer Prime (Sonic) It/Its/He/Him.
Slammer Amy It/Its/She/Her.

The final thing I will mention here is Slammer Prime's first computer/victim is indeed Tom, since Slammer is my take on Sonic.exe as a whole.
Tom his design and story will be worked on at a later date.
Thank you for reading, if you have any questions let me know!
#sonic.exe#sonic.exe au#sonic.exe oc#sql slammer worm#slammer sonic#slammer virus#lore#important#I've likely stated some things before#but it's good to have alot of info in one post
7 notes
·
View notes
Text
the way i spent hours and hours just trying to do one thing, but i finally got it

#it was important#i have an archive that list every unique boyfriend thats been added with there info like their name and an image of them#every time a new bf is claimed by a user#a separate bf is created for the 'boyfriend' table#(this is different from the archive because the boyfriend table has EVERY bf in existence on the site#every users boyfriends exist here)#so every time a bf was claimed i needed that specific row on the table to pull the image for that bf from the archive#omg i was fighting for my life trying to figure it out#i already knew about triggers so i wasnt super stuck there#i was stuck on trying to set up the actual sql query to pull the info i needed#BUT I GOT IT NOW WEE#now i can move to the next thing...#now i need to figure out how to make the website list only the bfs that belong to specific users#webdev#codeblr
0 notes
Text
Securing Your Website: Best Practices for Web Developers
As the digital landscape continues to evolve, website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated, it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this article, we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potential threats.
Introduction
In today's interconnected world, websites serve as the digital storefront for businesses, making them vulnerable targets for cyber attacks. From data breaches to malware infections, the consequences of a security breach can be severe, ranging from financial loss to damage to reputation. Therefore, prioritizing website security is essential for maintaining the trust and confidence of users.
Understanding Website Security
Before diving into best practices, it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measures taken to protect websites from cyber threats and unauthorized access. Common threats include malware infections, phishing attacks, SQL injection, cross-site scripting (XSS), and brute force attacks.
Best Practices for Web Developers
Keeping Software Updated
One of the most fundamental steps in website security is keeping all software, including the content management system (CMS), plugins, and server software, updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can be exploited.
Implementing HTTPS
Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users, ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors, as indicated by the padlock icon in the browser's address bar.
Using Strong Authentication Methods
Implementing strong authentication methods, such as multi-factor authentication (MFA) and CAPTCHA, adds an extra layer of security to user accounts. MFA requires users to provide multiple forms of verification, such as a password and a one-time code sent to their mobile device, reducing the risk of unauthorized access.
Securing Against SQL Injection Attacks
SQL injection attacks occur when malicious actors exploit vulnerabilities in web applications to execute arbitrary SQL commands. Web developers can prevent SQL injection attacks by using parameterized queries and input validation to sanitize user inputs effectively.
Protecting Sensitive Data
It's essential to employ encryption techniques to protect sensitive data, such as passwords, credit card information, and personal details, stored on the website's servers. Encrypting data at rest and in transit mitigates the risk of data breaches and unauthorized access.
Regular Security Audits
Conducting regular security audits helps identify vulnerabilities and weaknesses in the website's infrastructure and codebase. Penetration testing, vulnerability scanning, and code reviews enable web developers to proactively address security issues before they are exploited by attackers.
Choosing a Secure Hosting Provider
Selecting a reputable and secure hosting provider is critical for ensuring the overall security of your website. When evaluating hosting providers, consider factors such as security features, reliability, scalability, and customer support.
Evaluating Security Features
Choose a hosting provider that offers robust security features, such as firewalls, intrusion detection systems (IDS), malware scanning, and DDoS protection. These features help protect your website from various cyber threats and ensure continuous uptime.
Ensuring Regular Backups
Regularly backing up your website's data is essential for mitigating the impact of security incidents, such as data breaches or website compromises. Choose a hosting provider that offers automated backup solutions and store backups securely offsite.
Customer Support and Response to Security Incidents
Opt for a hosting provider that provides responsive customer support and has established protocols for handling security incidents. In the event of a security breach or downtime, prompt assistance from the hosting provider can minimize the impact on your website and business operations.
Implementing Firewall Protection
Firewalls act as a barrier between your website and external threats, filtering incoming and outgoing network traffic based on predefined security rules. There are several types of firewalls, including network firewalls, web application firewalls (WAF), and host-based firewalls.
Configuring and Maintaining Firewalls
Properly configuring and maintaining firewalls is crucial for effective security. Define firewall rules based on the principle of least privilege, regularly update firewall configurations to reflect changes in the website's infrastructure, and monitor firewall logs for suspicious activity.
Educating Users about Security
In addition to implementing technical measures, educating users about security best practices is essential for enhancing overall website security. Provide users with resources, such as security guidelines, tips for creating strong passwords, and information about common phishing scams.
Importance of User Awareness
Users play a significant role in maintaining website security, as they are often the targets of social engineering attacks. By raising awareness about potential threats and providing guidance on how to recognize and respond to them, web developers can empower users to stay vigilant online.
Providing Training and Resources
Offer training sessions and educational materials to help users understand the importance of security and how to protect themselves while using the website. Regularly communicate updates and reminders about security practices to reinforce good habits.
Monitoring and Responding to Security Incidents
Despite taking preventive measures, security incidents may still occur. Establishing robust monitoring systems and incident response protocols enables web developers to detect and respond to security threats in a timely manner.
Setting Up Monitoring Tools
Utilize monitoring tools, such as intrusion detection systems (IDS), security information and event management (SIEM) systems, and website monitoring services, to detect abnormal behavior and potential security breaches. Configure alerts to notify you of suspicious activity promptly.
Establishing Incident Response Protocols
Develop comprehensive incident response plans that outline roles, responsibilities, and procedures for responding to security incidents. Establish clear communication channels and escalation paths to coordinate responses effectively and minimize the impact of security breaches.
Securing your website requires a proactive approach that involves implementing a combination of technical measures, choosing a secure hosting provider, educating users about security best practices, and establishing robust monitoring and incident response protocols. By following these best practices, web developers can mitigate the risk of security breaches and safeguard their websites and the sensitive data they handle.
#website security has become a paramount concern for businesses and individuals alike. With cyber threats becoming increasingly sophisticated#it is crucial for web developers to adopt robust security measures to safeguard their websites and the sensitive data they handle. In this#we'll delve into the best practices that web developers can implement to enhance the security of their websites and protect against potenti#Introduction#In today's interconnected world#websites serve as the digital storefront for businesses#making them vulnerable targets for cyber attacks. From data breaches to malware infections#the consequences of a security breach can be severe#ranging from financial loss to damage to reputation. Therefore#prioritizing website security is essential for maintaining the trust and confidence of users.#Understanding Website Security#Before diving into best practices#it's crucial to understand the importance of website security and the common threats faced by websites. Website security encompasses measur#phishing attacks#SQL injection#cross-site scripting (XSS)#and brute force attacks.#Best Practices for Web Developers#Keeping Software Updated#One of the most fundamental steps in website security is keeping all software#including the content management system (CMS)#plugins#and server software#updated with the latest security patches and fixes. Outdated software is often targeted by attackers due to known vulnerabilities that can#Implementing HTTPS#Implementing HTTPS (Hypertext Transfer Protocol Secure) encrypts the data transmitted between the website and its users#ensuring confidentiality and integrity. HTTPS not only protects sensitive information but also boosts trust among visitors#as indicated by the padlock icon in the browser's address bar.#Using Strong Authentication Methods#Implementing strong authentication methods
0 notes
Text
Efficient Data Import in SQL Server 2022: BCP vs. BULK INSERT vs. OPENROWSET
Ever found yourself swimming in an ocean of data, wondering the best way to import it into your SQL Server? You’re not alone. SQL Server 2022 comes to the rescue with a trio of tools designed to streamline this process: BCP, BULK INSERT, and OPENROWSET. Each has its unique flair for handling data, and I’m here to guide you through choosing the right tool for the job with some handy T-SQL…
View On WordPress
#BCP command examples#BULK INSERT SQL tutorial#Efficient database management SQL#OPENROWSET usage guide#SQL Server 2022 data import
0 notes
Text
Get a solution for importing large SQL files in phpMyAdmin and optimize your database management for seamless performance. Let’s get started!
#how to import large sql file in phpmyadmin cpanel#how to import large sql file in phpmyadmin#import large sql file in phpmyadmin#phpmyadmin import large sql file#how to upload large sql file in phpmyadmin
0 notes
Text
Ok I've had a very random train of thoughts and now wanna compile it into post.
Some MM characters computer-related (???) headcanons lol
Riley:
Has above average knowledge of Excel/Google sheets due to studying finance, but after four years with no practise forgot most of it.
The "Sooon, I have a problem" person in their family. Actually, surprisingly good and patient at explaining computer stuff to older people.
Has a higher responsibility of doing taxes (finance, after all). Even he never fails to do them right, Ed always double checks. Sometimes they get into argument, where inevitably Riley proves he is right but his father would never admit it.
Warren, Leeza, Ooker and other teens:
Also nothing outstanding in terms of skills, except few of them have interest in IT.
They have bunch of small local Discord servers and one big main server with some very stupid name.
Few times Bev tried to bring up importance of parental control over this "new and rapidly growing young community", but thanks God no one took her concerns seriously
Leeza moderates it and her moder role called "Mayor-mini". Like father like daughter.
All teens local jokes and memes were bourn/spread though that server.
Bev:
Rumors says she sacrificed her humanity to obtain such powers with Microsoft software package.
Can build up Access database from scratch, using basic SQL commands, assemble primitive, but surprisingly sufficient interface to it and synchronize it with Excel in span of one day or less.
In her laptop there're every pupil's personal file, countless Excel tables, several automatised document accounts, Google calendar with precisely planned schedule for next several months (for school, church, island and personal matters) and probably Pentagon files.
Probably can find all Pi numbers with Excel formulas.
Never lets anyone to her laptop.
Spends her free time at different forums, mostly gardening-related.
Wade:
Made a very fucking poor decision to let Bev do all the legwork with digital document accounting.
Now has no idea how some of things even work, so just goes with a flow and does what Bev tells.
No wander she got away with embezzlement.
Knows about kid's server. Very proud of Leeza for managing it :)
Because of that, he knows one or two memes from there, but keeps them in secret.
Has hobby of fixing office equipment. Does it with Sturge in spare time due to Dupuytren's contracture not letting him operate his hand fully.
Sarah:
There's no good medical technicians on island, so when something goes wrong with equipment electronics - tries to fix it herself to best of her ability.
Always monitors electronic e-shops for spare details or equipment. Grows more and more addicted to it.
Frequently updates her selection of sites with useful medical information, because Erin asked her for help guiding teens though puberty. For that receives glances from Bev, but doesn't give a shit.
Has reputation of cool aunt among kids, so she was one and only adult invited to main Discord server. Didn't accept it (doesn't even have Discord acc), but still grateful for trust.
Plays solitaire a lot.
John:
Back when he was playing Paul, Bev asked him to do something with Excel. In conclusion, poor bastard had to learn basic computer skills and Excel in span of several days. Now he is traumatized for rest of his life.
Will do all the work manually just to not touch laptop again.
Upsets very easly when does something wrong.
Doesn't own laptop. Don't give that man laptop, he will cry.
By his own will uses it only to watch baseball. Always asks someone to help with that.
#midnight mass#midnight mass headcanons#beverly keane#idk I just felt silly and wanted to write it down#riley flynn#warren flynn#leeza scarborough#wade scarborough#sarah gunning#john pruitt#monsignor pruitt#father paul hill
24 notes
·
View notes
Text
Unlocking the Power of Data: Essential Skills to Become a Data Scientist

In today's data-driven world, the demand for skilled data scientists is skyrocketing. These professionals are the key to transforming raw information into actionable insights, driving innovation and shaping business strategies. But what exactly does it take to become a data scientist? It's a multidisciplinary field, requiring a unique blend of technical prowess and analytical thinking. Let's break down the essential skills you'll need to embark on this exciting career path.
1. Strong Mathematical and Statistical Foundation:
At the heart of data science lies a deep understanding of mathematics and statistics. You'll need to grasp concepts like:
Linear Algebra and Calculus: Essential for understanding machine learning algorithms and optimizing models.
Probability and Statistics: Crucial for data analysis, hypothesis testing, and drawing meaningful conclusions from data.
2. Programming Proficiency (Python and/or R):
Data scientists are fluent in at least one, if not both, of the dominant programming languages in the field:
Python: Known for its readability and extensive libraries like Pandas, NumPy, Scikit-learn, and TensorFlow, making it ideal for data manipulation, analysis, and machine learning.
R: Specifically designed for statistical computing and graphics, R offers a rich ecosystem of packages for statistical modeling and visualization.
3. Data Wrangling and Preprocessing Skills:
Raw data is rarely clean and ready for analysis. A significant portion of a data scientist's time is spent on:
Data Cleaning: Handling missing values, outliers, and inconsistencies.
Data Transformation: Reshaping, merging, and aggregating data.
Feature Engineering: Creating new features from existing data to improve model performance.
4. Expertise in Databases and SQL:
Data often resides in databases. Proficiency in SQL (Structured Query Language) is essential for:
Extracting Data: Querying and retrieving data from various database systems.
Data Manipulation: Filtering, joining, and aggregating data within databases.
5. Machine Learning Mastery:
Machine learning is a core component of data science, enabling you to build models that learn from data and make predictions or classifications. Key areas include:
Supervised Learning: Regression, classification algorithms.
Unsupervised Learning: Clustering, dimensionality reduction.
Model Selection and Evaluation: Choosing the right algorithms and assessing their performance.
6. Data Visualization and Communication Skills:
Being able to effectively communicate your findings is just as important as the analysis itself. You'll need to:
Visualize Data: Create compelling charts and graphs to explore patterns and insights using libraries like Matplotlib, Seaborn (Python), or ggplot2 (R).
Tell Data Stories: Present your findings in a clear and concise manner that resonates with both technical and non-technical audiences.
7. Critical Thinking and Problem-Solving Abilities:
Data scientists are essentially problem solvers. You need to be able to:
Define Business Problems: Translate business challenges into data science questions.
Develop Analytical Frameworks: Structure your approach to solve complex problems.
Interpret Results: Draw meaningful conclusions and translate them into actionable recommendations.
8. Domain Knowledge (Optional but Highly Beneficial):
Having expertise in the specific industry or domain you're working in can give you a significant advantage. It helps you understand the context of the data and formulate more relevant questions.
9. Curiosity and a Growth Mindset:
The field of data science is constantly evolving. A genuine curiosity and a willingness to learn new technologies and techniques are crucial for long-term success.
10. Strong Communication and Collaboration Skills:
Data scientists often work in teams and need to collaborate effectively with engineers, business stakeholders, and other experts.
Kickstart Your Data Science Journey with Xaltius Academy's Data Science and AI Program:
Acquiring these skills can seem like a daunting task, but structured learning programs can provide a clear and effective path. Xaltius Academy's Data Science and AI Program is designed to equip you with the essential knowledge and practical experience to become a successful data scientist.
Key benefits of the program:
Comprehensive Curriculum: Covers all the core skills mentioned above, from foundational mathematics to advanced machine learning techniques.
Hands-on Projects: Provides practical experience working with real-world datasets and building a strong portfolio.
Expert Instructors: Learn from industry professionals with years of experience in data science and AI.
Career Support: Offers guidance and resources to help you launch your data science career.
Becoming a data scientist is a rewarding journey that blends technical expertise with analytical thinking. By focusing on developing these key skills and leveraging resources like Xaltius Academy's program, you can position yourself for a successful and impactful career in this in-demand field. The power of data is waiting to be unlocked – are you ready to take the challenge?
3 notes
·
View notes
Text
USEFUL TIPS FOR ANYONE USING NEOCITIES
So, I saw this super awesome post called BEGINNERS GUIDE TO BLUESKY and it more or less inspired me to make a post of my own pertaining to the the likes of Neocities.
What is Neocities?
Long story short, it is an open-source web hosting service that is both F2U (1 GB storage/200 GB bandwidth) and P2U (50 GB storage/3000 GB bandwidth). It's kinda sorta a spiritual successor to the now defunct GeoCities.
Why Use Neocities?
HELPFUL LINKS
Neocities has a full on Tutorials Page to help people wanting to learning how to code. Though I will say that I'm a bit surprised they don't have W3 Schools on there.
CREATIVE FREEDOM
If you Browse on Neocities, you will see how vastly different all of the websites look. That being said, you have an enormous amount of creative freedom when it comes to making your website. You can build it from scratch or look up some pre-made templates from websites such as templatemo, HTML5 Templates, TEMPLATED, template4all, and many more.
Now it is important to note that Neocities doesn't allow certain things such as jQuery, PHP, Python, SQL, etc. In fact, the only things allowed on Neocities are HTML, CSS, and JavaScript! Though I do think it is important to note that you can turn your website into a blog using Zonelets, have a Guestbook/Comments Section with Guestbooks, embed your Bluesky feed with Embed Bsky, embed your Twitter/X feed with Twitter Publish, and much more!
What Do People Use Neocities For?
Some people use it for blogging & portfolio & educational purposes. Some people use it to share their writings & artwork & music. Some people use it to help people with finding neat things. Some people use it for shits and giggles. There are legitimately a number of reasons people use it and you know what? That's 100% a-okay!
Are Any Programs Required To Use Neocities?
Technically, no. The reason I say this is because Neocities has a built-in HTML Editor. However, I don't like using it unless if I absolutely have to (which is next to never). Instead, I use Brackets. It's very user-friendly and it legit lets you know if there's a goof somewhere in your code. Legit 10 out of 10 recommend. Though I will say that some people use Notepad++.
#pvposeur's tutorial#pvposeur's tutorials#pvposeur's how tos#pvposeur's how to#pvposeur's psa#pvposeur's public service announcements#pvposeur's public service announcement#tutorial#tutorials#how to#how tos#psa#public service announcements#public service announcement#neocities#free to reblog
2 notes
·
View notes
Text
Structured Query Language (SQL): A Comprehensive Guide
Structured Query Language, popularly called SQL (reported "ess-que-ell" or sometimes "sequel"), is the same old language used for managing and manipulating relational databases. Developed in the early 1970s by using IBM researchers Donald D. Chamberlin and Raymond F. Boyce, SQL has when you consider that end up the dominant language for database structures round the world.
Structured query language commands with examples
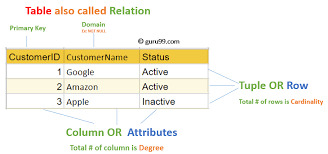
Today, certainly every important relational database control system (RDBMS)—such as MySQL, PostgreSQL, Oracle, SQL Server, and SQLite—uses SQL as its core question language.
What is SQL?
SQL is a website-specific language used to:
Retrieve facts from a database.
Insert, replace, and delete statistics.
Create and modify database structures (tables, indexes, perspectives).
Manage get entry to permissions and security.
Perform data analytics and reporting.
In easy phrases, SQL permits customers to speak with databases to shop and retrieve structured information.
Key Characteristics of SQL
Declarative Language: SQL focuses on what to do, now not the way to do it. For instance, whilst you write SELECT * FROM users, you don’t need to inform SQL the way to fetch the facts—it figures that out.
Standardized: SQL has been standardized through agencies like ANSI and ISO, with maximum database structures enforcing the core language and including their very own extensions.
Relational Model-Based: SQL is designed to work with tables (also called members of the family) in which records is organized in rows and columns.
Core Components of SQL
SQL may be damaged down into numerous predominant categories of instructions, each with unique functions.
1. Data Definition Language (DDL)
DDL commands are used to outline or modify the shape of database gadgets like tables, schemas, indexes, and so forth.
Common DDL commands:
CREATE: To create a brand new table or database.
ALTER: �� To modify an present table (add or put off columns).
DROP: To delete a table or database.
TRUNCATE: To delete all rows from a table but preserve its shape.
Example:
sq.
Copy
Edit
CREATE TABLE personnel (
id INT PRIMARY KEY,
call VARCHAR(one hundred),
income DECIMAL(10,2)
);
2. Data Manipulation Language (DML)
DML commands are used for statistics operations which include inserting, updating, or deleting information.
Common DML commands:
SELECT: Retrieve data from one or more tables.
INSERT: Add new records.
UPDATE: Modify existing statistics.
DELETE: Remove information.
Example:
square
Copy
Edit
INSERT INTO employees (id, name, earnings)
VALUES (1, 'Alice Johnson', 75000.00);
three. Data Query Language (DQL)
Some specialists separate SELECT from DML and treat it as its very own category: DQL.
Example:
square
Copy
Edit
SELECT name, income FROM personnel WHERE profits > 60000;
This command retrieves names and salaries of employees earning more than 60,000.
4. Data Control Language (DCL)
DCL instructions cope with permissions and access manage.
Common DCL instructions:
GRANT: Give get right of entry to to users.
REVOKE: Remove access.
Example:
square
Copy
Edit
GRANT SELECT, INSERT ON personnel TO john_doe;
five. Transaction Control Language (TCL)
TCL commands manage transactions to ensure data integrity.
Common TCL instructions:
BEGIN: Start a transaction.
COMMIT: Save changes.
ROLLBACK: Undo changes.
SAVEPOINT: Set a savepoint inside a transaction.
Example:
square
Copy
Edit
BEGIN;
UPDATE personnel SET earnings = income * 1.10;
COMMIT;
SQL Clauses and Syntax Elements
WHERE: Filters rows.
ORDER BY: Sorts effects.
GROUP BY: Groups rows sharing a assets.
HAVING: Filters companies.
JOIN: Combines rows from or greater tables.
Example with JOIN:
square
Copy
Edit
SELECT personnel.Name, departments.Name
FROM personnel
JOIN departments ON personnel.Dept_id = departments.Identity;
Types of Joins in SQL
INNER JOIN: Returns statistics with matching values in each tables.
LEFT JOIN: Returns all statistics from the left table, and matched statistics from the right.
RIGHT JOIN: Opposite of LEFT JOIN.
FULL JOIN: Returns all records while there is a in shape in either desk.
SELF JOIN: Joins a table to itself.
Subqueries and Nested Queries
A subquery is a query inside any other query.
Example:
sq.
Copy
Edit
SELECT name FROM employees
WHERE earnings > (SELECT AVG(earnings) FROM personnel);
This reveals employees who earn above common earnings.
Functions in SQL
SQL includes built-in features for acting calculations and formatting:
Aggregate Functions: SUM(), AVG(), COUNT(), MAX(), MIN()
String Functions: UPPER(), LOWER(), CONCAT()
Date Functions: NOW(), CURDATE(), DATEADD()
Conversion Functions: CAST(), CONVERT()
Indexes in SQL
An index is used to hurry up searches.
Example:
sq.
Copy
Edit
CREATE INDEX idx_name ON employees(call);
Indexes help improve the performance of queries concerning massive information.
Views in SQL
A view is a digital desk created through a question.
Example:
square
Copy
Edit
CREATE VIEW high_earners AS
SELECT call, salary FROM employees WHERE earnings > 80000;
Views are beneficial for:
Security (disguise positive columns)
Simplifying complex queries
Reusability
Normalization in SQL
Normalization is the system of organizing facts to reduce redundancy. It entails breaking a database into multiple related tables and defining overseas keys to link them.
1NF: No repeating groups.
2NF: No partial dependency.
3NF: No transitive dependency.
SQL in Real-World Applications
Web Development: Most web apps use SQL to manipulate customers, periods, orders, and content.
Data Analysis: SQL is extensively used in information analytics systems like Power BI, Tableau, and even Excel (thru Power Query).
Finance and Banking: SQL handles transaction logs, audit trails, and reporting systems.
Healthcare: Managing patient statistics, remedy records, and billing.
Retail: Inventory systems, sales analysis, and consumer statistics.
Government and Research: For storing and querying massive datasets.
Popular SQL Database Systems
MySQL: Open-supply and extensively used in internet apps.
PostgreSQL: Advanced capabilities and standards compliance.
Oracle DB: Commercial, especially scalable, agency-degree.
SQL Server: Microsoft’s relational database.
SQLite: Lightweight, file-based database used in cellular and desktop apps.
Limitations of SQL
SQL can be verbose and complicated for positive operations.
Not perfect for unstructured information (NoSQL databases like MongoDB are better acceptable).
Vendor-unique extensions can reduce portability.
Java Programming Language Tutorial
Dot Net Programming Language
C ++ Online Compliers
C Language Compliers
2 notes
·
View notes
Text
What is Lead Generation? A Complete Guide for Beginners in 2025
In the ever-evolving world of digital marketing and sales, lead generation remains a foundational strategy for business growth. Whether you’re running a small startup or a large enterprise, understanding what lead generation is—and how to do it effectively—can make or break your customer acquisition efforts.
In this post, we’ll break down what lead generation means, how it works, why it’s important in 2025, and how you can start implementing a successful lead generation strategy today.
What is Lead Generation?
Lead generation is the process of attracting and converting strangers into someone who has indicated interest in your product or service. These individuals are called "leads" and are typically the first step in the sales funnel.
A lead can be anyone who has shared their contact information with your business—whether by filling out a form, subscribing to a newsletter, downloading an eBook, or booking a demo.
The goal of lead generation is simple: build a pipeline of potential customers and nurture them into becoming paying clients.

Why Lead Generation is Crucial in 2025
With buyers becoming more informed and self-directed, the way businesses generate leads has shifted significantly. According to Demand Gen Report (source), 71% of B2B buyers start their journey with a generic search. This makes it more important than ever for businesses to have a strong online presence and provide value from the very first interaction.
Here’s why lead generation is essential in today’s landscape:
It drives business growth: Without leads, you have no sales. And without sales, you have no business.
It builds relationships: Lead generation introduces people to your brand in a helpful, non-intrusive way.
It improves ROI: Targeted lead gen strategies ensure you’re attracting the right audience, not wasting resources.
It supports long-term success: A consistent lead pipeline means predictable revenue and scalable growth.
Types of Leads
Not all leads are the same. Understanding the different types can help you tailor your messaging and approach.
1. Marketing Qualified Lead (MQL)
Someone who has shown interest through content interaction but isn’t ready to buy yet.
2. Sales Qualified Lead (SQL)
A lead who has taken action suggesting they’re ready to talk to your sales team (like booking a call).
3. Product Qualified Lead (PQL)
Typically relevant for SaaS—someone who has used your product (like a free trial) and shows buying intent.
How Lead Generation Works
The lead generation process usually includes these key steps:
1. Attract Visitors
Use SEO, social media, content marketing, and paid ads to bring people to your website or landing pages.
2. Offer Value
Create lead magnets like guides, webinars, checklists, or free tools that your target audience wants.
3. Capture Information
Use forms, chatbots, or popups to collect user details in exchange for your lead magnet.
4. Nurture and Convert
Send follow-up emails, offer more content, or schedule calls to move leads further down the funnel.
Watch: What is Lead Generation?
📹 This beginner-friendly YouTube video explains it well: "7 Keys to Lead Generation & Sales Prospecting for Business Development and B2B Sales"
youtube
Popular Lead Generation Strategies in 2025
✍️ Content Marketing
Publishing helpful blog posts, whitepapers, or videos to attract and educate potential customers.
🔍 Search Engine Optimization (SEO)
Optimizing your site and content to rank high on Google so your target audience can find you.
📧 Email Marketing
Sending personalized, value-packed messages to nurture leads and keep them engaged.
💼 LinkedIn Outreach
Great for B2B businesses—use it to connect with decision-makers and share valuable resources.
📣 Paid Advertising
Run targeted ads on Google, Facebook, or LinkedIn to bring traffic directly to high-converting landing pages.
Tools to Help with Lead Generation
Here are some must-have tools to streamline your lead generation efforts:
HubSpot – CRM and marketing automation for capturing and nurturing leads.
Mailchimp – For sending and automating email campaigns.
OptinMonster – Great for creating popups and opt-in forms.
SEMrush – For keyword research and SEO optimization.
LinkedIn Sales Navigator – Ideal for identifying and connecting with B2B leads.
How Businesses Use Lead Generation Services
Many companies choose to outsource their efforts to experts who specialize in attracting and converting high-quality leads. These lead generation services offer tailored strategies that align with your industry, audience, and growth goals—saving time while maximizing ROI.
Final Thoughts
Lead generation is the lifeblood of any successful business. Whether you’re a marketer trying to fill your sales funnel or an entrepreneur looking to grow your client base, understanding how to attract and convert leads is essential.
By combining valuable content, smart targeting, and nurturing tools, you can build a lead gen system that works for you 24/7. In 2025, the businesses that thrive will be the ones that focus not just on selling—but on providing value from the very first click.
2 notes
·
View notes
Text
Why Tableau is Essential in Data Science: Transforming Raw Data into Insights

Data science is all about turning raw data into valuable insights. But numbers and statistics alone don’t tell the full story—they need to be visualized to make sense. That’s where Tableau comes in.
Tableau is a powerful tool that helps data scientists, analysts, and businesses see and understand data better. It simplifies complex datasets, making them interactive and easy to interpret. But with so many tools available, why is Tableau a must-have for data science? Let’s explore.
1. The Importance of Data Visualization in Data Science
Imagine you’re working with millions of data points from customer purchases, social media interactions, or financial transactions. Analyzing raw numbers manually would be overwhelming.
That’s why visualization is crucial in data science:
Identifies trends and patterns – Instead of sifting through spreadsheets, you can quickly spot trends in a visual format.
Makes complex data understandable – Graphs, heatmaps, and dashboards simplify the interpretation of large datasets.
Enhances decision-making – Stakeholders can easily grasp insights and make data-driven decisions faster.
Saves time and effort – Instead of writing lengthy reports, an interactive dashboard tells the story in seconds.
Without tools like Tableau, data science would be limited to experts who can code and run statistical models. With Tableau, insights become accessible to everyone—from data scientists to business executives.
2. Why Tableau Stands Out in Data Science
A. User-Friendly and Requires No Coding
One of the biggest advantages of Tableau is its drag-and-drop interface. Unlike Python or R, which require programming skills, Tableau allows users to create visualizations without writing a single line of code.
Even if you’re a beginner, you can:
✅ Upload data from multiple sources
✅ Create interactive dashboards in minutes
✅ Share insights with teams easily
This no-code approach makes Tableau ideal for both technical and non-technical professionals in data science.
B. Handles Large Datasets Efficiently
Data scientists often work with massive datasets—whether it’s financial transactions, customer behavior, or healthcare records. Traditional tools like Excel struggle with large volumes of data.
Tableau, on the other hand:
Can process millions of rows without slowing down
Optimizes performance using advanced data engine technology
Supports real-time data streaming for up-to-date analysis
This makes it a go-to tool for businesses that need fast, data-driven insights.
C. Connects with Multiple Data Sources
A major challenge in data science is bringing together data from different platforms. Tableau seamlessly integrates with a variety of sources, including:
Databases: MySQL, PostgreSQL, Microsoft SQL Server
Cloud platforms: AWS, Google BigQuery, Snowflake
Spreadsheets and APIs: Excel, Google Sheets, web-based data sources
This flexibility allows data scientists to combine datasets from multiple sources without needing complex SQL queries or scripts.
D. Real-Time Data Analysis
Industries like finance, healthcare, and e-commerce rely on real-time data to make quick decisions. Tableau’s live data connection allows users to:
Track stock market trends as they happen
Monitor website traffic and customer interactions in real time
Detect fraudulent transactions instantly
Instead of waiting for reports to be generated manually, Tableau delivers insights as events unfold.
E. Advanced Analytics Without Complexity
While Tableau is known for its visualizations, it also supports advanced analytics. You can:
Forecast trends based on historical data
Perform clustering and segmentation to identify patterns
Integrate with Python and R for machine learning and predictive modeling
This means data scientists can combine deep analytics with intuitive visualization, making Tableau a versatile tool.
3. How Tableau Helps Data Scientists in Real Life
Tableau has been adopted by the majority of industries to make data science more impactful and accessible. This is applied in the following real-life scenarios:
A. Analytics for Health Care
Tableau is deployed by hospitals and research institutions for the following purposes:
Monitor patient recovery rates and predict outbreaks of diseases
Analyze hospital occupancy and resource allocation
Identify trends in patient demographics and treatment results
B. Finance and Banking
Banks and investment firms rely on Tableau for the following purposes:
✅ Detect fraud by analyzing transaction patterns
✅ Track stock market fluctuations and make informed investment decisions
✅ Assess credit risk and loan performance
C. Marketing and Customer Insights
Companies use Tableau to:
✅ Track customer buying behavior and personalize recommendations
✅ Analyze social media engagement and campaign effectiveness
✅ Optimize ad spend by identifying high-performing channels
D. Retail and Supply Chain Management
Retailers leverage Tableau to:
✅ Forecast product demand and adjust inventory levels
✅ Identify regional sales trends and adjust marketing strategies
✅ Optimize supply chain logistics and reduce delivery delays
These applications show why Tableau is a must-have for data-driven decision-making.
4. Tableau vs. Other Data Visualization Tools
There are many visualization tools available, but Tableau consistently ranks as one of the best. Here’s why:
Tableau vs. Excel – Excel struggles with big data and lacks interactivity; Tableau handles large datasets effortlessly.
Tableau vs. Power BI – Power BI is great for Microsoft users, but Tableau offers more flexibility across different data sources.
Tableau vs. Python (Matplotlib, Seaborn) – Python libraries require coding skills, while Tableau simplifies visualization for all users.
This makes Tableau the go-to tool for both beginners and experienced professionals in data science.
5. Conclusion
Tableau has become an essential tool in data science because it simplifies data visualization, handles large datasets, and integrates seamlessly with various data sources. It enables professionals to analyze, interpret, and present data interactively, making insights accessible to everyone—from data scientists to business leaders.
If you’re looking to build a strong foundation in data science, learning Tableau is a smart career move. Many data science courses now include Tableau as a key skill, as companies increasingly demand professionals who can transform raw data into meaningful insights.
In a world where data is the driving force behind decision-making, Tableau ensures that the insights you uncover are not just accurate—but also clear, impactful, and easy to act upon.
#data science course#top data science course online#top data science institute online#artificial intelligence course#deepseek#tableau
3 notes
·
View notes
Text
In Microsoft SQL Server, stored procedures (SP) are crucial for implementing business logic according to the organization’s requirements, enhancing query efficiency, and securing important data. Let's Explore Deeply:
https://madesimplemssql.com/sql-stored-procedure/
Follow us on FB: https://www.facebook.com/profile.php?id=100091338502392
2 notes
·
View notes
Text
Top 5 Programming Languages to Master in 2025
Programming language theory is the subfield of computer science that studies the design, implementation, analysis, characterization, and classification of programming languages.
1. Java
You might ask, “Is Java obsolete?” Of course not.
Why is Java still popular? Java is one of the oldest and most robust programming languages. It is also an object-oriented language mainly used for Android application development. This is one of the main reasons it is still used today. However, with the advent of programming languages like Kotlin (also suitable for Android development), Java is becoming less popular.

2. Swift

3. SQL
4. JavaScript

5. Python

The amazing thing about Python is that it’s a general-purpose programming language used to build a wide range of applications. Furthermore, it is active in artificial intelligence. Self-driving cars, Wal-Mart auto-payment, and many automation and machine learning (ML) apps were developed through Python. This makes this language more important and rapidly popularizes. In addition, Python is easier to learn than all other languages and is easy for beginners. You can also build complex applications relatively easily and quickly. In the United States, the average salary for Python developers is about $ 78,000, while experienced developers can be as high as $ 122,000.
2 notes
·
View notes
Text
Protect Your Laravel APIs: Common Vulnerabilities and Fixes
API Vulnerabilities in Laravel: What You Need to Know
As web applications evolve, securing APIs becomes a critical aspect of overall cybersecurity. Laravel, being one of the most popular PHP frameworks, provides many features to help developers create robust APIs. However, like any software, APIs in Laravel are susceptible to certain vulnerabilities that can leave your system open to attack.

In this blog post, we’ll explore common API vulnerabilities in Laravel and how you can address them, using practical coding examples. Additionally, we’ll introduce our free Website Security Scanner tool, which can help you assess and protect your web applications.
Common API Vulnerabilities in Laravel
Laravel APIs, like any other API, can suffer from common security vulnerabilities if not properly secured. Some of these vulnerabilities include:
>> SQL Injection SQL injection attacks occur when an attacker is able to manipulate an SQL query to execute arbitrary code. If a Laravel API fails to properly sanitize user inputs, this type of vulnerability can be exploited.
Example Vulnerability:
$user = DB::select("SELECT * FROM users WHERE username = '" . $request->input('username') . "'");
Solution: Laravel’s query builder automatically escapes parameters, preventing SQL injection. Use the query builder or Eloquent ORM like this:
$user = DB::table('users')->where('username', $request->input('username'))->first();
>> Cross-Site Scripting (XSS) XSS attacks happen when an attacker injects malicious scripts into web pages, which can then be executed in the browser of a user who views the page.
Example Vulnerability:
return response()->json(['message' => $request->input('message')]);
Solution: Always sanitize user input and escape any dynamic content. Laravel provides built-in XSS protection by escaping data before rendering it in views:
return response()->json(['message' => e($request->input('message'))]);
>> Improper Authentication and Authorization Without proper authentication, unauthorized users may gain access to sensitive data. Similarly, improper authorization can allow unauthorized users to perform actions they shouldn't be able to.
Example Vulnerability:
Route::post('update-profile', 'UserController@updateProfile');
Solution: Always use Laravel’s built-in authentication middleware to protect sensitive routes:
Route::middleware('auth:api')->post('update-profile', 'UserController@updateProfile');
>> Insecure API Endpoints Exposing too many endpoints or sensitive data can create a security risk. It’s important to limit access to API routes and use proper HTTP methods for each action.
Example Vulnerability:
Route::get('user-details', 'UserController@getUserDetails');
Solution: Restrict sensitive routes to authenticated users and use proper HTTP methods like GET, POST, PUT, and DELETE:
Route::middleware('auth:api')->get('user-details', 'UserController@getUserDetails');
How to Use Our Free Website Security Checker Tool
If you're unsure about the security posture of your Laravel API or any other web application, we offer a free Website Security Checker tool. This tool allows you to perform an automatic security scan on your website to detect vulnerabilities, including API security flaws.
Step 1: Visit our free Website Security Checker at https://free.pentesttesting.com. Step 2: Enter your website URL and click "Start Test". Step 3: Review the comprehensive vulnerability assessment report to identify areas that need attention.
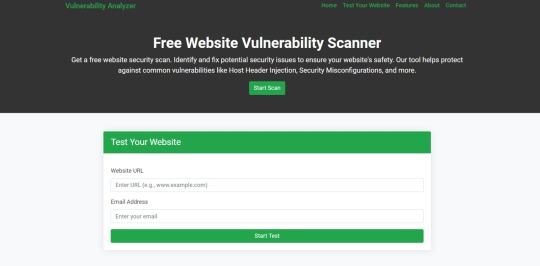
Screenshot of the free tools webpage where you can access security assessment tools.
Example Report: Vulnerability Assessment
Once the scan is completed, you'll receive a detailed report that highlights any vulnerabilities, such as SQL injection risks, XSS vulnerabilities, and issues with authentication. This will help you take immediate action to secure your API endpoints.
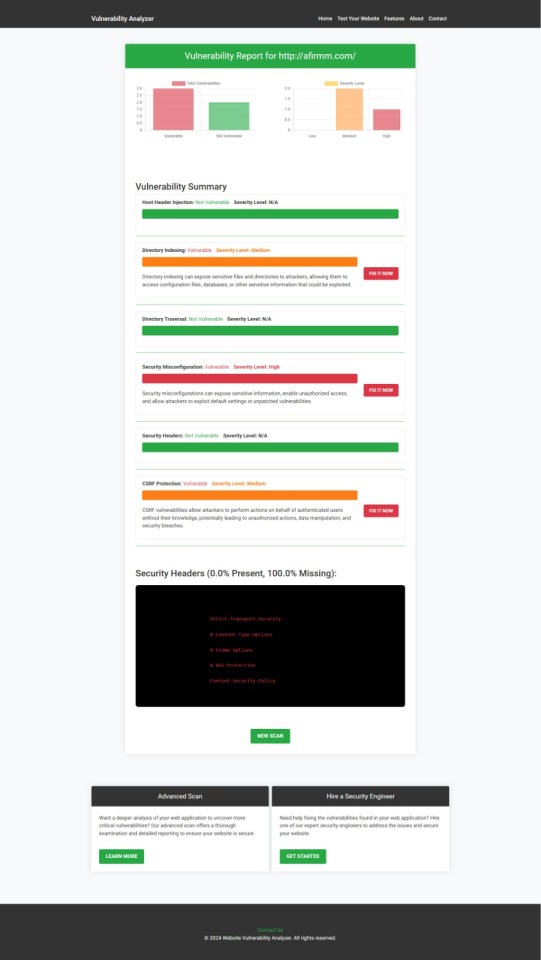
An example of a vulnerability assessment report generated with our free tool provides insights into possible vulnerabilities.
Conclusion: Strengthen Your API Security Today
API vulnerabilities in Laravel are common, but with the right precautions and coding practices, you can protect your web application. Make sure to always sanitize user input, implement strong authentication mechanisms, and use proper route protection. Additionally, take advantage of our tool to check Website vulnerability to ensure your Laravel APIs remain secure.
For more information on securing your Laravel applications try our Website Security Checker.
#cyber security#cybersecurity#data security#pentesting#security#the security breach show#laravel#php#api
2 notes
·
View notes
Text
Choosing Between SQL Server Destination and OLE DB Destination in SSIS: Performance & Flexibility
When working with SQL Server Integration Services (SSIS) to perform data integration and ETL (Extract, Transform, Load) tasks, you might encounter various destination components that allow you to write data to SQL Server. Two common components are the SQL Server Destination and the OLE DB Destination. Understanding the differences between these two can help you choose the appropriate component…
View On WordPress
0 notes